Risk Based Approach: Boost Compliance Today
Published: May 6, 2025The Strategic Foundations of Risk-Based Approaches
A risk-based approach focuses resources on significant threats. It does not treat all risks the same. This proactive strategy optimizes how resources are used. It ensures critical vulnerabilities get the attention they need.
This is different from traditional compliance frameworks. Those often use a “checklist” mentality. This can waste resources on low-impact areas while critical vulnerabilities go unaddressed.
This shift in focus marks a major change. Organizations are rethinking their compliance and security strategies.
Understanding the Core Principles
Successful risk-based approaches depend on accurate risk assessment. This means identifying potential threats and analyzing their likelihood and impact.
For example, consider a company that stores sensitive customer data. A data breach would have a much bigger impact than a minor equipment malfunction. This assessment helps allocate resources effectively, ensuring critical risks receive priority.
Adaptability is also important. New threats require a flexible approach that adjusts priorities.
Evolution of Risk-Based Approaches
The risk-based approach (RBA) keeps evolving. In anti-money laundering (AML) and combating the financing of terrorism (CFT), RBA has gained importance. Initially introduced in the 2003 FATF Recommendations, it became essential in the revised 2012 Recommendations.
This approach guides financial institutions to focus on high-risk areas. These include customers, transactions, and regions with the greatest risk of financial crime. Tailoring compliance efforts helps organizations mitigate threats and optimize resources. For example, politically exposed persons (PEPs) and high-value transactions need enhanced due diligence. Learn more about the evolution of RBA in AML/CFT.
Benefits of a Risk-Based Approach
Adopting a risk-based approach offers many benefits. It strengthens security by focusing on critical issues. It also streamlines operations by cutting unnecessary efforts on low-impact risks. This leads to better security outcomes with greater efficiency.
Additionally, a risk-based approach allows for proactive risk management. Identifying and addressing threats early can reduce their impact or even prevent incidents. This approach also improves compliance. It aligns efforts with regulatory requirements that emphasize risk-based methods. Moving from checkbox compliance to real risk management is key to modern compliance programs.
Financial Compliance: Where Risk-Based Approach Shines
Financial institutions were early adopters of the risk-based approach to compliance. The potential costs of non-compliance, like hefty fines and reputational damage, drive this. This has led to risk assessment frameworks that align controls with actual risk profiles, improving resource allocation while maintaining security.
Client, Transaction, and Geographic Risk Categorization
Modern institutions are shifting from broad policies. They categorize clients, transactions, and geographic areas by inherent risk. This allows for more targeted and effective resource use.
A high-value transaction from a high-risk area will receive more scrutiny. In contrast, a small domestic transaction from a long-term client may need less oversight. This ensures resources are directed where they are most needed.
Transforming Customer Due Diligence
The risk-based approach is changing how we view Customer Due Diligence (CDD). Smart onboarding workflows use data analysis and automation to assess client risk from the start. This enables tailored ongoing monitoring.
Adaptive monitoring systems adjust scrutiny levels based on new risk signals. This lets institutions respond to changing risk profiles, enhancing both security and efficiency. Think of it as a targeted security system that focuses on unusual activity.
Evolving Regulatory Expectations
Regulators now seek risk intelligence, not just checklist compliance. They expect financial institutions to understand their specific risks and implement effective risk-based programs. This means moving beyond basic compliance to a data-driven, active risk management approach. Such a proactive stance benefits both the individual institutions and the broader financial system.
Demonstrating Program Effectiveness
Proving that a risk-based program works is crucial. This involves documenting the risk assessment process, the reasoning behind risk categories, and the effectiveness of the controls. Transparency is essential for showing a strong compliance program. Regulators also appreciate evidence of ongoing program improvement and adaptation.
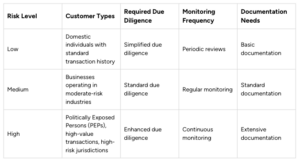
Risk Stratification in Action
To illustrate how this works in practice, the following table shows how organizations tailor their compliance activities based on the level of risk. This targeted approach saves resources and strengthens security.
Risk Stratification Framework: Actions Required by Risk Level
This comprehensive breakdown shows exactly how leading organizations tailor their compliance activities based on risk categorization, saving resources while enhancing security
This targeted approach allows institutions to use their resources more effectively. By focusing on the biggest risks, financial institutions can protect themselves and their clients while optimizing their compliance work. This contributes to a safer and more secure financial system overall.
Cybersecurity Transformation Through Risk-Based Approach
In today’s complex threat landscape, equally protecting every asset is risky. It spreads resources thin and weakens security. A risk-based approach offers a smarter strategy. It focuses on protecting your most valuable assets and tackling critical vulnerabilities. This targeted strategy lets security teams concentrate their efforts, maximizing their impact and strengthening defenses.
Identifying and Prioritizing Critical Assets
The key to a risk-based approach is identifying your crown jewel assets. These are essential for your organization’s survival, like sensitive customer data and critical infrastructure. Once identified, security teams can assess the fallout from a potential compromise. This step guides how to allocate resources effectively.
Identifying critical vulnerabilities is also vital. These weaknesses in your systems could let attackers access those valuable assets. A risk-based approach treats vulnerabilities differently, focusing on those that pose the greatest threat.
Implementing Practical Frameworks
Leading security teams use practical frameworks like threat modeling, vulnerability assessments, and impact analysis. Threat modeling helps identify potential threats and their methods. This enables security teams to build defenses against likely attack vectors. Vulnerability assessments find weaknesses before attackers can exploit them. Impact analysis shows the possible consequences of a breach, helping organizations make informed decisions on risk mitigation. This proactive strategy enhances an organization’s ability to respond quickly to new threats.
By 2027, cybercrime could cost the global economy nearly $24 trillion. A risk-based strategy identifies, prioritizes, and mitigates cybersecurity risks. This method is more effective than traditional approaches, aligning cybersecurity measures with an organization’s risk profile. Techniques like risk quantification aid in making smart resource allocation decisions. This proactive approach builds resilience, crucial for tackling dynamic cyber threats.
Developing Adaptive Security Controls
Effective risk management needs adaptive security controls. These controls adjust to changing risk levels. For instance, if a system sees a sudden spike in suspicious activity, adaptive controls might boost monitoring or restrict access. This keeps resources focused on urgent threats.
Measurable Improvements and Reduced Spending
Risk-based security programs show measurable improvements in protection while cutting unnecessary costs. By focusing on critical risks, organizations gain a higher security level without needing more resources. This results in better security and increased cost-effectiveness, making a strong case for a risk-based approach.
Public Safety Revolution: Risk-Based Emergency Response
When lives are at stake, efficient resource allocation is crucial. This means positioning personnel, equipment, and funding where they can have the most impact. A risk-based approach is transforming emergency services and disaster management. It uses data to enhance public safety, shifting from reacting to incidents to anticipating and mitigating risks.
Data-Driven Risk Assessments
Progressive agencies leverage data to understand and prioritize risks better. They analyze historical incident data, geographic information, demographic trends, and real-time sensor data. This helps identify areas with the highest risk of incidents and potential losses. For example, a coastal community may emphasize flood preparedness, while an urban area focuses on fire risks.
This data-driven model helps emergency services optimize equipment deployment, staffing, and response protocols. It shifts from reactive to proactive, positioning resources to tackle the most likely impactful events.
Balancing Community Expectations and Resource Constraints
Adopting a risk-based approach requires balancing community expectations with limited resources. While communities want maximum protection, agencies must focus on the most critical risks. Clear communication with stakeholders about risk assessments builds trust. It helps the public understand why some areas receive more attention.
This approach acknowledges that not all risks can be managed equally. It prioritizes significant threats, ensuring resources are used effectively for better community outcomes.
Considering Low-Probability, High-Impact Events
The risk-based approach also considers low-probability, high-impact events. These rare “black swan” events can have severe consequences. Agencies need frameworks to evaluate and prepare for these scenarios, even if they fall outside typical risk assessments.
In fire prevention, this approach assesses fire hazards and allocates resources accordingly. The U.S. Fire Administrator’s Summit discussed using a risk-based approach for PPE selection and distribution among first responders, especially during shortages. The summit raised issues like technological advancements in fire causes and personnel shortages in fire departments. The focus is on optimizing resource allocation for urgent risks.
Protecting Vulnerable Populations and Critical Infrastructure
A risk-based approach recognizes that some populations and infrastructure are more vulnerable to specific threats. For instance, elderly residents may be especially at risk during heat waves, while hospitals and power plants need increased security. This targeted approach leads to specific interventions and resource allocation, enhancing community resilience. By focusing on these vulnerabilities, resources are directed where they can make the most difference, improving public safety and building a stronger community.
Transforming Audit Programs With Risk-Based Intelligence
The era of routine audits is fading. Today’s effective audits rely on risk-based intelligence. This method directs resources to high-impact areas, focusing on the most significant potential issues. This shift represents a move toward proactive auditing, emphasizing risk anticipation and mitigation rather than reaction.
Understanding Risk Assessment Frameworks
Revamping an audit program starts with understanding the risk assessment process. Establish a clear framework for evaluating various elements, including financial materiality, a company’s past compliance history, and the complexity of the system being audited.
For example, a system managing significant financial transactions with compliance issues is higher risk than a simple, compliant system. This thorough evaluation allows for better resource distribution in audits.
Balancing Coverage and Efficiency
A core challenge in adopting a risk-based approach is balancing coverage and resource efficiency. Leading organizations find this balance using a tiered system. High-risk areas undergo more frequent audits, while lower-risk areas are monitored less often.
This targeted strategy maximizes audit effectiveness, ensuring resources are used wisely. It also allows auditors to delve deeper into high-risk areas, uncovering hidden vulnerabilities. All areas receive appropriate oversight while focusing on critical concerns.
Risk-Based Auditing in Federal Programs
A risk-based approach is vital in auditing and financial management, especially for identifying high-risk areas in federal programs. Auditors must use this method to prioritize major programs needing focused audits. This involves assessing factors like financial stability, system management quality, and historical performance.
By focusing on high-risk areas, agencies can allocate resources more effectively.
Communicating Risk Performance to Stakeholders
Communicating risk performance to different stakeholders is essential. Technical teams need detailed data analysis, while executives require concise summaries of key trends and impacts. Visualizations, like dashboards and charts, can make complex data actionable. Clear communication ensures everyone understands the organization’s risk posture and the value of the risk-based program.
To understand how to measure the success of risk-based programs, review the following table. It provides a structured way to track progress and demonstrate the impact of such programs.
Performance Metrics Matrix for Risk Based Programs
This comprehensive framework breaks down exactly how to measure the effectiveness of risk-based approaches across different organizational functions.
By tracking these metrics, organizations can prove the effectiveness of their risk-based approaches. This data-driven approach allows for continuous improvement and shows the program’s value. This focus on continuous improvement ensures risk management programs adapt and stay effective against evolving risks.
Ready to transform your KYC and investor onboarding? Blackbird automates compliance workflows, accelerates due diligence, and reduces manual effort, ensuring fast and accurate compliance checks. Learn more about how Blackbird can help your organization at blackbrd.co