AML Compliance Checklist: Ensure Your Business Stays Ahead
Published: May 8, 2025Navigating the Complexities of AML Compliance
This AML compliance checklist provides eight essential components for building a robust program, mitigating financial crime risks, and protecting your institution. From Customer Due Diligence (CDD) and Enhanced Due Diligence (EDD) to sanctions screening and independent audits, this list covers the core requirements for effective AML compliance. By understanding these key areas, your organization can navigate regulatory complexities and safeguard its reputation. This checklist offers a practical roadmap for achieving AML compliance in 2025 and beyond.
1. Customer Due Diligence (CDD)
Customer Due Diligence (CDD) is a cornerstone of any effective AML compliance checklist. It’s a critical process for verifying customer identities and assessing their risk profiles. This involves collecting and analyzing relevant information to understand who customers are, their business activities, and their expected transaction patterns. This information is crucial for establishing a risk baseline, which is then used for ongoing monitoring and helps financial institutions mitigate the risk of facilitating money laundering and terrorist financing. A robust CDD program is not just a regulatory requirement; it’s essential for protecting the institution’s reputation and financial stability.
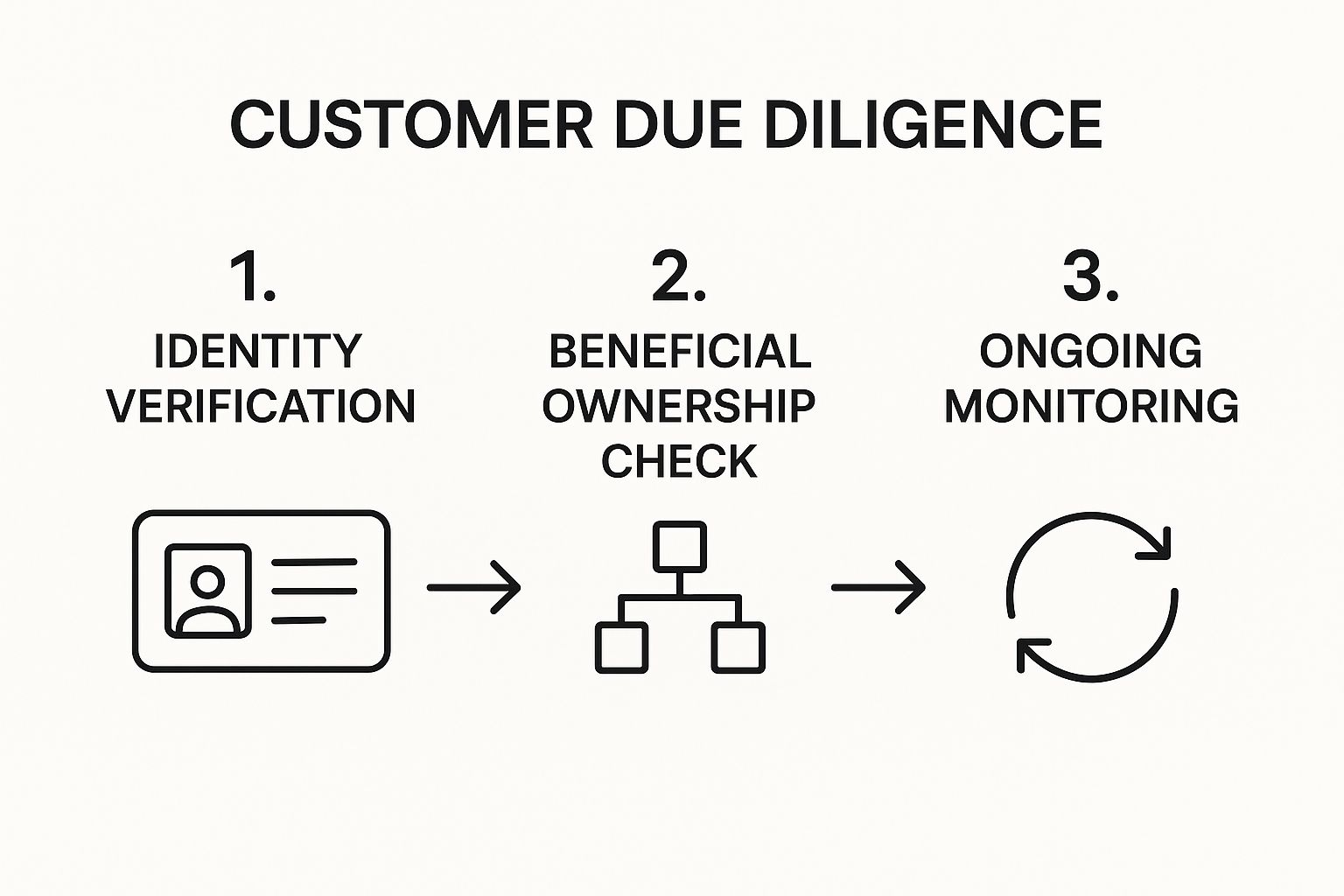
The infographic above shows the typical CDD process flow. It starts with identifying customers and goes through risk assessment, ongoing monitoring, and record-keeping. This highlights that CDD is a continuous process, not a one-time event.
CDD has several key features. It includes identity verification using government-issued documents. It also means finding out who truly owns legal entities. This helps reveal hidden ownership. A risk-based approach tailors the depth of verification to the customer’s risk level. There are ongoing monitoring requirements for changes in customer behavior or risk profile. Additionally, it adheres to KYC (Know Your Customer) protocols. This approach allows institutions to use resources wisely, focusing on higher-risk customers.
The CDD process follows a structured workflow. It begins with customer identification and data collection. This means gathering details like name, address, date of birth, and identification documents. Then, the customer’s risk profile is assessed based on their business activities, location, and transaction history. This assessment helps determine the level of due diligence needed. We monitor customer transactions for suspicious behavior. If we find anything unusual, we investigate further. Finally, careful record-keeping ensures compliance with regulations and provides an audit trail. This sequence is crucial for effectively identifying and managing risk throughout the customer relationship.
To implement CDD successfully, strong policies, trained staff, and advanced technology are vital. For instance, HSBC uses Robotic Process Automation to streamline CDD processes, boosting efficiency and cutting costs. Chase Bank uses a digital identity verification system. It checks documents and uses biometrics. This shows how technology improves customer due diligence (CDD).
Pros of Implementing CDD:
- Prevents criminals from accessing financial services: By verifying identities and assessing risk, CDD makes it more difficult for criminals to use financial institutions for illicit purposes.
- Enables accurate risk assessment of customers: CDD provides the information necessary to categorize customers based on their risk level.
- Forms the foundation for transaction monitoring: The baseline created during CDD is essential for effective transaction monitoring.
- Helps fulfill regulatory requirements: A strong CDD program is crucial for complying with AML regulations.
Cons of Implementing CDD:
- Can create friction in customer onboarding: The information gathering process can sometimes be perceived as lengthy or complex by customers.
- May require significant resources for proper implementation: Building and maintaining a comprehensive CDD program requires investment in personnel, technology, and training.
- Requires regular updates and reviews: Regulations and best practices evolve, requiring ongoing updates to CDD policies and procedures.
- Can be seen as invasive by some customers: Collecting detailed personal and financial information can raise privacy concerns for some customers.
Actionable Tips for Effective CDD:
- Implement a tiered approach based on risk levels: Focus resources on higher-risk customers.
- Leverage technology for efficient document verification and identity checks: Automate processes where possible.
- Maintain a centralized customer data repository: This allows for a holistic view of each customer.
- Document CDD procedures clearly for consistent application: Ensure all staff understand and follow established procedures.
- Create escalation procedures for high-risk cases: Define clear protocols for handling potentially suspicious activity.
CDD is popularized and mandated by international bodies such as the Financial Action Task Force (FATF), guided by principles from the Wolfsberg Group, and enforced through legislation like the Bank Secrecy Act (BSA). Its prominent place on any AML compliance checklist is undeniable due to its crucial role in mitigating financial crime risks and upholding the integrity of the financial system. For compliance professionals, a thorough understanding and effective implementation of CDD is paramount.
2. Enhanced Due Diligence (EDD)
Enhanced Due Diligence (EDD) is vital for a strong AML compliance checklist. It targets high-risk customers. This helps reduce financial crimes, such as money laundering and terrorist financing.
High-risk customers include:
-
Politically Exposed Persons (PEPs)
-
Individuals in risky areas
-
Businesses with complex ownership
-
Those involved in large transactions
EDD goes beyond standard Customer Due Diligence (CDD) by examining the source of funds, wealth, and business activities. This thorough approach helps institutions assess a customer’s true risk and take necessary measures.
EDD has key features that distinguish it from standard CDD. It needs extra verification steps. This often means providing documents and confirming customer information independently. Senior management usually needs to approve onboarding and ongoing ties with high-risk customers. EDD also demands careful verification of the source of funds and wealth. This includes tracking asset origins and confirming their legitimacy. Ongoing enhanced monitoring is crucial too. This means closely examining transactions and regularly reviewing the customer’s profile, typically more frequently than for lower-risk customers.
Pros of Implementing EDD:
- Stronger protection against financial crime risks: By深入挖掘客户背景和资金来源, EDD helps identify and mitigate potential risks more effectively.
- Demonstrates regulatory commitment: Robust EDD processes demonstrate a strong commitment to AML compliance to regulators and supervisors.
- Creates deeper understanding of high-risk customers: This allows for more informed decision-making and relationship management.
- Enables more precise risk management: By accurately assessing risk, institutions can allocate resources more efficiently and focus on the most critical threats.
Cons of Implementing EDD:
- Resource-intensive process: EDD requires significant time, effort, and specialized expertise.
- May create significant onboarding delays: The extensive checks involved can prolong the onboarding process, potentially impacting customer satisfaction.
- Requires specialized staff training: Personnel handling EDD cases need specific training and experience in areas such as risk assessment, investigation, and regulatory requirements.
- Potentially intrusive for legitimate customers: The increased scrutiny can be perceived as intrusive by legitimate customers, potentially damaging business relationships.
Examples of Successful EDD Implementation:
- Standard Chartered Bank has specialized EDD teams dedicated to international correspondent banking, a particularly high-risk area.
- Goldman Sachs utilizes dedicated PEP monitoring systems to track and manage relationships with politically exposed persons.
Tips for Effective EDD Implementation:
- Develop clear triggers for EDD: Establish specific criteria that automatically trigger EDD, ensuring consistency and minimizing subjective judgment.
- Create specialized teams: Assemble teams with the necessary expertise and experience to handle complex EDD cases.
- Document rationale for risk decisions: Maintain detailed records of the risk assessment process and the rationale behind EDD decisions.
- Implement automated screening: Use automated systems to screen customers against PEP and sanctions lists, streamlining the process and improving efficiency.
- Establish clear approval authorities and escalation paths: Define clear roles and responsibilities for approving high-risk customers and escalating potential issues.
EDD’s importance within the AML compliance checklist is underscored by its prominence in international regulations and industry best practices. The USA PATRIOT Act, the EU’s Anti-Money Laundering Directives, and the Wolfsberg Group principles all emphasize the need for enhanced scrutiny of high-risk customers. By implementing a robust EDD program, financial institutions can effectively manage risk, protect their reputation, and contribute to the global fight against financial crime. This proactive approach is essential for fulfilling regulatory obligations and maintaining the integrity of the financial system.
3. Transaction Monitoring Systems
Transaction monitoring systems are crucial for an effective AML compliance checklist. They help combat financial crime by watching customer transactions in real-time. This allows them to identify suspicious activities or patterns that may suggest money laundering or terrorist financing. By analyzing large volumes of transaction data, these systems flag risky transactions for compliance teams. This process helps institutions reduce risk and comply with regulations.
These systems use rules-based detection alongside machine learning. Pre-defined rules catch known money laundering cases, while machine learning identifies unusual customer behavior. This combination enhances the system’s ability to find both familiar and new threats. Key features include:
-
Rules-based detection
-
Machine learning anomaly detection
-
Alert management systems
-
Risk scoring
-
Case management
-
Detailed audit trails for regulatory proof
These features assist compliance teams in managing investigations, prioritizing alerts, and demonstrating compliance efforts to regulators.
Transaction monitoring systems should be a priority in any AML compliance checklist. They handle large transaction volumes and apply detection rules consistently. This fast identification of potential red flags minimizes human error. Real-time monitoring provides a significant advantage in rapidly changing financial environments, enabling institutions to respond quickly to suspicious activity. These systems can also adjust to new risks through regular updates and tuning.
Examples of Successful Implementation:
- HSBC: HSBC’s implementation of AI-powered transaction monitoring has reportedly reduced false positives by 20%, demonstrating the potential for advanced analytics to improve efficiency and accuracy.
- Danske Bank: In the wake of a major money laundering scandal, Danske Bank overhauled its AML compliance program, implementing advanced behavioral analytics as a central component of its transaction monitoring system.
Pros:
- Ability to process vast transaction volumes
- Consistent application of detection rules
- Real-time or near-real-time monitoring capabilities
- Adaptability to emerging typologies and risks
Cons:
- High false positive rates in many implementations
- Significant initial and ongoing investment
- Requires regular tuning and optimization
- Effectiveness depends on quality of underlying data
Tips for Effective Implementation:
- Regularly tune thresholds: This helps reduce false positives and ensures that alerts are focused on truly suspicious activity.
- Implement feedback loops: Incorporate insights from investigations back into the system configuration to refine detection scenarios and improve accuracy.
- Ensure comprehensive data feeds: Integrate data from all relevant systems to provide a holistic view of customer activity.
- Regular testing: Conduct regular testing with typology-based scenarios to validate the system’s effectiveness.
- Maintain documentation: Thoroughly document all system configuration changes for audit and regulatory purposes.
Popularized By: NICE Actimize, Oracle Financial Services, Fiserv, FinCEN guidance documents
When and why should you use this approach? Transaction monitoring systems are essential for any organization that processes financial transactions and is subject to AML regulations. This includes banks, financial institutions, payment processors, and other businesses handling customer funds. By incorporating a robust transaction monitoring system into your AML compliance checklist, you can significantly enhance your ability to detect and prevent financial crime, mitigate regulatory risk, and protect your institution’s reputation.
4. Suspicious Activity Reporting
Suspicious Activity Reporting (SAR) is a crucial element of any robust AML compliance checklist. It is the process of identifying, investigating, documenting, and reporting potentially suspicious transactions or activities to the appropriate financial intelligence unit (FIU), such as FinCEN in the United States. This is not merely a best practice; it’s a legal requirement in most jurisdictions and serves as a critical component in the global fight against financial crimes like money laundering and terrorist financing. Therefore, incorporating a strong SAR process is essential for any organization subject to AML regulations.
How it Works:
The SAR process typically involves several key steps:
- Identification: Employees across the organization, particularly those on the front lines, are trained to recognize red flags that may indicate suspicious activity. These red flags can include unusual transaction patterns, large cash deposits, wire transfers to high-risk jurisdictions, or customer behavior that deviates from established norms.
- Investigation: Once a potential red flag is identified, a trained investigator gathers information to determine whether the activity is truly suspicious. This may involve reviewing customer records, transaction histories, open-source intelligence, and other relevant data.
- Documentation: The investigation process must be thoroughly documented, including all evidence gathered, analysis performed, and rationale for the decision to file or not file a SAR.
- Reporting: If the investigation concludes that the activity is suspicious, a SAR is filed with the appropriate FIU, following the prescribed format and timeframe.
- Feedback and Tuning: FIUs may provide feedback on filed SARs, allowing institutions to refine their detection and reporting processes. Ongoing monitoring and analysis of SAR trends are also vital for improving the effectiveness of the AML program.
Features of a Robust SAR Program:
- Investigation workflows: Clearly defined processes for escalating and investigating suspicious activity.
- Documentation requirements: Standardized templates and procedures for documenting investigations.
- Filing mechanisms for regulatory reports: Secure and reliable systems for submitting SARs to the FIU.
- Decision-making frameworks: Clear guidelines for determining whether to file a SAR.
- Quality assurance processes: Reviews of filed SARs to ensure accuracy and completeness.
- Confidentiality safeguards: Protection of sensitive information related to SARs.
Pros:
- Creates audit trail of compliance efforts: Demonstrates to regulators that the institution takes AML compliance seriously.
- Contributes to broader financial crime detection: Provides valuable intelligence to law enforcement agencies.
- Protects institution from regulatory penalties: Reduces the risk of fines and other sanctions for non-compliance.
- Demonstrates good corporate citizenship: Shows a commitment to combating financial crime.
Cons:
- Resource-intensive investigation requirements: Can be costly and time-consuming to conduct thorough investigations.
- Legal risks if filing obligations are mishandled: Failure to file a SAR or filing an inaccurate SAR can result in significant penalties.
- Difficult to measure effectiveness: The impact of SAR filings on financial crime detection is not always readily apparent.
- Potential for defensive filing: Institutions may file SARs out of an abundance of caution, even when the activity is not truly suspicious, to avoid potential liability.
Examples of Successful Implementation:
- JP Morgan’s implementation of AI-assisted investigation processes has streamlined their SAR workflow and improved efficiency.
- Wells Fargo’s centralized investigation unit structure, implemented following regulatory actions, enhances oversight and consistency in SAR filings.
Tips for Effective SAR Implementation:
- Establish clear escalation paths and decision authorities: Ensure that all employees understand their roles and responsibilities in the SAR process.
- Implement robust case management systems: Track and manage SAR investigations efficiently.
- Create comprehensive investigation templates: Standardize data collection and analysis.
- Develop quality review processes for filed reports: Minimize errors and ensure accuracy.
- Train investigators on emerging typologies: Stay up-to-date on the latest money laundering and terrorist financing techniques.
Why SARs Deserve Their Place in the AML Compliance Checklist:
SARs are the cornerstone of AML compliance. They provide a vital link between financial institutions and law enforcement in the fight against financial crime. For the Chief Compliance Officer, Head of Compliance, Compliance Director, CFO, or Investor Relations Manager, a robust SAR program is not just a regulatory requirement; it is a demonstration of the institution’s commitment to ethical and responsible business practices. By effectively identifying and reporting suspicious activity, institutions contribute to the global effort to combat financial crime and protect the integrity of the financial system.
5. Risk Assessment Framework
A robust Risk Assessment Framework is a cornerstone of any effective AML compliance checklist. This systematic approach forms the bedrock of a risk-based approach, enabling institutions to allocate resources efficiently and demonstrate regulatory compliance. It involves identifying, assessing, and documenting money laundering and terrorist financing risks across all facets of the organization: customers, products, services, channels, and geographic locations. Ignoring this crucial step can lead to ineffective controls, regulatory scrutiny, and potential financial penalties. This is why a thorough Risk Assessment Framework deserves its place on this AML compliance checklist.
How it Works:
The Risk Assessment Framework functions by systematically analyzing potential vulnerabilities. This begins with establishing an entity-level risk assessment methodology, which sets the overall tone and approach for the organization. Subsequently, various risk scoring models are employed, focusing on:
- Customer Risk Scoring: Evaluating individual customer profiles based on factors like transaction history, geographic location, industry, and customer due diligence information.
- Product/Service Risk Evaluation: Analyzing the inherent risks associated with specific products and services offered, such as cash-intensive services or complex international transactions.
- Geographic Risk Factors: Assessing risks linked to specific geographic locations, considering factors like political stability, corruption levels, and prevalence of financial crime.
- Channel and Delivery Method Risk Analysis: Examining the risks associated with different transaction channels, including online banking, mobile payments, and branch transactions.
These assessments incorporate both quantitative data (e.g., transaction volume, customer demographics) and qualitative factors (e.g., regulatory environment, expert opinions). The output is a comprehensive risk profile, identifying inherent risks (before controls) and residual risks (after controls).
Features:
- Entity-level risk assessment methodology
- Customer risk scoring models
- Product/service risk evaluation
- Geographic risk factors
- Channel and delivery method risk analysis
- Quantitative and qualitative assessment components
Pros:
- Enables efficient resource allocation: Focusing resources on higher-risk areas.
- Provides justification for control decisions: Demonstrates the rationale behind specific AML measures.
- Creates foundation for risk-based approach: Enables tailored AML programs based on identified risks.
- Demonstrates regulatory compliance: Provides evidence of a proactive approach to AML.
Cons:
- Complex to design and implement comprehensively: Requires significant expertise and resources.
- Requires regular updates as risks evolve: The risk landscape is constantly changing, necessitating ongoing review and updates.
- Depends on quality of underlying data and assumptions: Inaccurate data can lead to flawed assessments.
- May be challenging to quantify certain risks: Some risks, particularly reputational risks, can be difficult to express numerically.
Examples of Successful Implementation:
- Citigroup: Utilizes an enterprise-wide risk assessment methodology spanning over 160 countries, enabling a globally consistent approach to risk management.
- Barclays: Employs a dynamic risk scoring system that adapts to changing customer behaviors, ensuring continuous risk monitoring.
Actionable Tips:
- Document methodology and assumptions thoroughly: Transparency is crucial for internal review and regulatory examinations.
- Include both inherent and residual risk assessments: This demonstrates the effectiveness of implemented controls.
- Update at least annually and after major changes: Regular reviews ensure the framework remains relevant and accurate.
- Ensure business line input and ownership: Involving relevant stakeholders promotes buy-in and improves accuracy.
- Map controls to identified risks: Demonstrates how specific controls mitigate specific risks.
Popularized By:
- Financial Action Task Force (FATF) recommendations
- Wolfsberg Group risk assessment principles
- Federal Financial Institutions Examination Council (FFIEC)
By diligently implementing a Risk Assessment Framework, financial institutions can strengthen their AML compliance posture, optimize resource allocation, and effectively mitigate the risks of money laundering and terrorist financing. This proactive approach is essential for fulfilling regulatory obligations and maintaining the integrity of the financial system.
6. Sanctions Screening Program
A robust sanctions screening program is a non-negotiable component of any effective AML compliance checklist. This system screens customers and transactions against constantly evolving global sanctions lists, helping financial institutions avoid hefty penalties and reputational damage associated with doing business with sanctioned individuals, entities, or countries. Its inclusion in your AML compliance checklist is crucial for demonstrating regulatory compliance and protecting your institution’s financial integrity.
How it Works:
A sanctions screening program operates by comparing customer data (names, addresses, etc.) and transaction details against lists of sanctioned parties published by various authorities, such as the Office of Foreign Assets Control (OFAC), UN Security Council sanctions committees, and EU sanctions authorities. This comparison happens through both real-time screening (during onboarding or transactions) and batch screening (periodically against the entire customer database). Sophisticated name-matching algorithms, often employing fuzzy logic, help identify potential matches even with slight variations in spelling or transliteration. List management functionality ensures the screening database is up-to-date with the latest sanctions, while alert handling workflows streamline investigation and reporting processes.
Features of an Effective Sanctions Screening Program:
- Real-time and Batch Screening: Covering both immediate transactions and periodic reviews.
- Name Matching Algorithms: Including fuzzy logic to catch variations and misspellings.
- List Management Functionality: Ensuring the use of current and comprehensive sanctions lists.
- Alert Handling Workflows: Providing structured processes for investigating potential matches.
- Screening Coverage Across Customer Lifecycle: From onboarding to ongoing monitoring.
Why Use a Sanctions Screening Program?
Sanctions violations can result in severe penalties, as demonstrated by BNP Paribas’ $8.9 billion fine. A robust sanctions screening program is a proactive measure to avoid such repercussions. It provides a systematic approach to sanctions compliance, demonstrating a commitment to regulatory requirements. This protects your institution’s reputation and minimizes the risk of financial losses.
Pros:
- Prevents costly sanctions violations.
- Creates a systematic approach to sanctions compliance.
- Demonstrates regulatory compliance to authorities.
- Protects the institution’s reputation and brand.
Cons:
- High false positive rates are common, requiring investigation and resolution.
- Complex implementation across multiple systems can be challenging.
- Requires frequent updates to sanctions lists from various sources.
- May impact transaction processing speed depending on the system’s efficiency.
Examples of Successful Implementation:
- BNP Paribas: While their massive penalty highlights the consequences of failures, their subsequent comprehensive overhaul serves as a case study in building a robust program.
- Standard Chartered: Their implementation of AI-enhanced screening demonstrates the potential for technology to reduce false positives and improve efficiency, reportedly achieving a 70% reduction.
Actionable Tips for Implementation:
- Comprehensive Integration: Implement screening at all customer touchpoints, including onboarding, KYC updates, and transactions.
- Regular Testing: Regularly test the effectiveness of your screening system with various scenarios and data sets.
- Clear Escalation Procedures: Develop clear escalation procedures for potential matches, outlining roles and responsibilities.
- Document Everything: Maintain thorough documentation of false positive resolution rationale for audit trails.
- Beneficial Ownership: Ensure screening covers beneficial owners and related parties to prevent circumvention of sanctions.
Data Providers and Authorities:
Key data providers for sanctions lists include Dow Jones, LexisNexis, and Refinitiv. Staying informed of updates from the Office of Foreign Assets Control (OFAC), UN Security Council sanctions committees, and EU sanctions authorities is vital for maintaining a compliant program.
This comprehensive approach to sanctions screening is essential for any organization operating in the international financial landscape and rightly deserves its place on the AML compliance checklist. By addressing the complexities and potential pitfalls with a well-defined program, your institution can minimize risk and maintain its reputation for regulatory compliance.
7. AML Training Program
A robust AML training program is a cornerstone of any effective AML compliance checklist. It’s a comprehensive education initiative designed to equip all relevant employees with the knowledge and skills necessary to identify and mitigate anti-money laundering (AML) risks. This includes understanding regulatory requirements and their specific responsibilities in preventing financial crime. Effective training is not just a regulatory requirement; it’s crucial for fostering a culture of compliance within the organization, protecting its reputation, and avoiding costly penalties.
A comprehensive AML training program should encompass several key features: role-specific training modules tailored to individual responsibilities, regular refresher courses to reinforce knowledge, assessments to gauge understanding, real-world case studies and examples for practical application, coverage of regulatory updates, and meticulous tracking and documentation of completion. When developing and implementing your program, especially when hiring new employees, understanding the legal guidelines for background checks is crucial for ensuring compliance from the outset. These guidelines, provided by SpringVerify, offer valuable insights into navigating the legal landscape of background checks in India, a critical component of a comprehensive AML compliance program.
This approach offers several advantages. It creates frontline awareness of potential red flags, demonstrating a strong commitment to regulatory compliance. It also develops a robust institutional knowledge base and supports a culture of compliance throughout the organization.
However, AML training programs also present challenges. Measuring their effectiveness beyond mere completion rates can be difficult. The program requires regular updates to stay relevant in the face of evolving regulations and criminal methodologies. Without strong leadership emphasis, training can be perceived as a mere checkbox exercise. Finally, developing and maintaining a truly effective program can be resource-intensive.
Successful implementations of AML training programs include HSBC’s global initiative following their 2012 deferred prosecution agreement, and Goldman Sachs’ interactive scenario-based training approach. These examples highlight the importance of a comprehensive and engaging training program.
To maximize the impact of your AML training program, consider these tips: tailor training content to specific roles and risk exposures; incorporate practical examples relevant to your business lines; use recent internal cases (where appropriate) as learning examples; develop metrics beyond completion rates to assess true understanding and behavioral change; and ensure board and senior management participation to demonstrate commitment from the top down. These measures contribute significantly to a more robust and effective AML compliance checklist.
The importance of AML training is underscored by organizations like the Association of Certified Anti-Money Laundering Specialists (ACAMS), the International Compliance Association (ICA), and the Financial Action Task Force (FATF), which all advocate for robust and continuous training in the fight against financial crime. Including a well-structured AML training program in your aml compliance checklist is crucial for mitigating risk, fostering a culture of compliance, and safeguarding your organization’s reputation.
8. Independent Testing and Audit
A robust AML compliance program isn’t a “set it and forget it” endeavor. Regular evaluation is critical to ensure ongoing effectiveness and adaptability to evolving risks. This is where independent testing and audit, a crucial component of any AML compliance checklist, comes into play. This process involves a thorough examination of your AML program by qualified, independent parties who are not involved in its day-to-day operations. These assessments provide an unbiased perspective and identify control gaps, compliance deficiencies, and opportunities for enhancement, offering valuable assurance to leadership, regulators, and stakeholders. This crucial step reinforces the integrity of your program and demonstrates your commitment to regulatory compliance.
How it Works:
Independent testing and audit involves a systematic review of various aspects of your AML program. This includes:
- Program governance assessment: Evaluating the overall framework, policies, procedures, and reporting structures.
- Control testing methodology: Examining the design and operating effectiveness of key controls, such as customer due diligence (CDD), enhanced due diligence (EDD), and suspicious activity reporting (SAR) processes.
- Transaction testing samples: Analyzing a representative sample of transactions to identify potential red flags and assess the effectiveness of transaction monitoring systems.
- Documentation review procedures: Verifying the adequacy and accuracy of supporting documentation for CDD, EDD, and SARs.
- Risk-based testing approach: Focusing resources on higher-risk areas, such as specific customer segments, geographies, or products/services.
- Remediation tracking mechanisms: Monitoring the implementation and effectiveness of corrective actions to address identified deficiencies.
Examples of Successful Implementation:
Several major financial institutions have effectively integrated independent testing and audit into their AML compliance programs. JPMorgan Chase, for instance, employs a “three lines of defense” model, which includes a dedicated AML testing team as the third line. Citibank leverages continuous monitoring technology alongside periodic independent testing to provide ongoing assurance.
Why Independent Testing and Audit Deserves its Place on the AML Compliance Checklist:
Independent testing provides an objective, unbiased assessment of your program’s effectiveness. Internal reviews can be subject to bias and may overlook critical vulnerabilities. By bringing in external expertise, you gain a fresh perspective and identify weaknesses that internal teams might miss. This proactive approach allows you to remediate issues before they are discovered by regulators, reducing the risk of fines, penalties, and reputational damage. Furthermore, the independent audit process creates accountability for program maintenance and demonstrates a strong commitment to regulatory compliance.
Pros:
- Identifies control weaknesses before regulators
- Provides objective assessment of program effectiveness
- Creates accountability for program maintenance
- Demonstrates regulatory commitment
Cons:
- Resource-intensive process
- May create tension with business and compliance teams
- Findings require resource commitment to address
- Scope limitations may miss emerging risks
Actionable Tips:
- Ensure true independence of the testing function: Avoid conflicts of interest by utilizing an external firm or a truly independent internal team.
- Develop risk-based testing plans: Prioritize areas with higher inherent risk.
- Maintain a tracking system for findings and remediation: Document identified issues, corrective actions, and their effectiveness.
- Include transaction testing alongside control assessment: Examine real-world transactions to assess the practical application of controls.
- Engage external specialists for periodic independent perspective: Bring in specialized expertise for complex areas such as sanctions compliance or cryptocurrency transactions.
Popularized By:
The importance of independent testing and audit is recognized by leading organizations such as the Institute of Internal Auditors (IIA), Big Four accounting firms (Deloitte, EY, KPMG, PwC), and the Federal Financial Institutions Examination Council (FFIEC).
When and Why to Use This Approach:
Independent testing and audit should be a regular component of your AML compliance program. The frequency of these assessments should be determined by your risk profile, regulatory requirements, and the complexity of your business. It’s essential to conduct these reviews at least annually, or more frequently if significant changes occur within your organization or the regulatory landscape. This consistent evaluation is crucial for maintaining a robust and effective AML program and protecting your organization from financial crime.
AML Compliance Checklist Comparison
Staying Ahead in the AML Game
Navigating the complexities of AML compliance can feel like a daunting task, but by focusing on the key elements outlined in this AML compliance checklist, your institution can establish a robust and effective program. From implementing thorough Customer Due Diligence (CDD) and Enhanced Due Diligence (EDD) procedures to leveraging sophisticated Transaction Monitoring Systems and ensuring timely Suspicious Activity Reporting, each step plays a vital role in mitigating risk. Remember, a comprehensive AML program also necessitates a strong Risk Assessment Framework, a robust Sanctions Screening Program, regular AML Training Programs, and routine Independent Testing and Audits.
Mastering these core components isn’t just about checking boxes; it’s about building a culture of compliance that protects your institution from financial crime, reputational damage, and regulatory penalties. By proactively addressing these areas, you contribute to a more secure financial ecosystem while demonstrating your commitment to ethical and responsible business practices. A strong AML compliance program fosters trust with investors, strengthens your reputation within the industry, and ultimately contributes to a safer financial world for everyone.
A technology-driven approach to your AML compliance checklist is crucial for staying ahead of evolving criminal methodologies. Streamline your processes and enhance your compliance posture with Blackbird, a cutting-edge platform designed to simplify and automate AML operations. Explore how Blackbird can empower your institution to manage risk effectively and efficiently by visiting Blackbird today.