Enhanced Due Diligence Checklist: 7 Essential Items for 2025
Published: July 8, 2025Navigating the Complexities of Enhanced Due Diligence
This guide lists 7 key Enhanced Due Diligence (EDD) measures. These steps help compliance officers reduce financial crime risks and meet global regulations.
This checklist outlines seven steps to lower financial crime risk. Chief Compliance Officers, CFOs, and Investor Relations Managers need to grasp these elements. This knowledge is vital for compliance and protecting your firm. From verifying customer identities and sources of funds to ongoing monitoring, this list ensures a strong approach to KYC. To improve your enhanced due diligence process and protect your organization, follow these steps.
1. What is Customer Identity Verification and why is it important?
Verifying customer identity and screening backgrounds are key parts of a solid EDD checklist. In today’s financial landscape, verifying high-risk customers is crucial. It helps reduce fraud, protect reputation, and avoid penalties. This process is more than just basic Know Your Customer (KYC) checks. It looks closely at a customer’s background, financial activities, and risks.
This verification process uses various data sources to create a complete picture of the customer. It begins by checking personal details, such as your name, date of birth, and address. This is done using trustworthy government records. The scope includes more than just basic checks. It looks at work history, checks financial activity, and screens for global sanctions and watchlists. This layered method helps find red flags. These may include inconsistencies in the information given or connections to known criminals. Third-party verification services improve this process. They provide access to specialized databases. You can also get expert help with document verification and biometric identification. Biometric verification boosts security. It checks facial recognition or fingerprints against official documents for precise identification. This scrutiny is crucial for high-risk customers. This includes politically exposed persons (PEPs), high-net-worth individuals, and people in high-risk areas.
Many institutions have successfully adopted strong customer identity verification programs. HSBC has improved its KYC program for private banking clients. It now includes several verification steps. Also, there is ongoing monitoring to ensure compliance and lower risk. JPMorgan Chase has a layered verification process for wealthy clients. It uses advanced analytics and monitors activities in real time. Deutsche Bank’s program for screening politically exposed persons demonstrates strong due diligence. These examples highlight how crucial a good customer screening process is, especially for high-risk clients.
While thorough customer identity verification has clear benefits, some drawbacks exist. The process can be time-consuming, delaying customer onboarding and affecting experience. Additionally, using multiple verification services and advanced technologies can raise costs. Customers may find the process intrusive or complicated, leading to abandonment. Balancing security and customer experience is vital for effective enhanced due diligence. Data privacy is also a significant concern. Collecting and storing customer data needs strong protection measures. This is important for following privacy rules and keeping trust.
To make your enhanced due diligence program more effective and lower risks, use these helpful tips:
-
Use automated verification tools. They can simplify the process and reduce manual work. Automated identity checks and background checks make things easier.
-
Implement risk-based approaches: Tailor the level of scrutiny to the customer’s perceived risk. Low-risk customers may need fewer checks than high-risk ones.
-
Maintain clear communication with customers: Transparency is essential. Explain the verification requirements to customers. Let them know why this process matters. It helps build trust.
-
Update verification databases often. This keeps your screening process accurate. Stay informed about changing rules, too.
Add strong Customer Identity Verification and Background Screening to your due diligence checklist. This step is key for thoroughness. With financial crime and regulation on the rise, organizations need to prioritize customer vetting. This protects both the organization and its clients. This proactive approach will not only reduce risk but also help create a more secure and transparent financial ecosystem.
2. Source of Wealth and Funds Documentation
Source of Wealth and Funds Documentation is crucial for any enhanced due diligence (EDD) checklist. It reviews a customer’s financial history to confirm where their wealth originates and the funds they will use in business. This process goes beyond standard KYC checks. We need to closely examine the customer’s finances. This helps reduce risks tied to money laundering, terrorist financing, and other financial crimes. Adding this to an EDD checklist is crucial for groups handling high-risk customers or transactions.
This investigation looks at all documents to track the customer’s wealth. It looks at different sources. These documents include income statements, tax returns, business ownership records, and inheritance papers. They also cover investment portfolios and other key financial records. The goal is to create a clear, auditable trail that shows the legitimate origin of the customer’s wealth and funds. This scrutiny helps identify red flags and lowers the risk of facilitating illegal activities.
How Source of Wealth and Funds Documentation Works:
The process starts with gathering basic information about the customer’s main wealth sources. Then, supporting documents are examined. If a customer says their wealth is from a successful business, investigators check company registration documents, financial statements, and tax filings. They may also conduct site visits or interviews with business associates. If the wealth is from inheritance, probate records, wills, and trust documents will be checked. Investment portfolios are analyzed to ensure they match the declared wealth profile.
Features of Effective Source of Wealth and Funds Documentation:
-
Comprehensive financial history analysis: Review historical financial records over several years to understand long-term wealth growth.
-
Tax return and income statement review: Verify declared income against official tax records to ensure consistency and spot discrepancies.
-
Business ownership and asset documentation: Examine business records, ownership structure, revenue streams, and asset holdings to confirm claims of business-related wealth.
-
Inheritance and gift documentation verification: Validate inheritance documents, such as wills and probate records, to confirm legitimate wealth transfers.
-
Investment portfolio analysis and tracking: Analyze the composition of funds in an investment portfolio to verify investment-related wealth.
Benefits of Implementing Robust Source of Wealth and Funds Documentation:
-
Prevents money laundering and illicit fund integration: Verifying the source of funds helps deter criminals from using services for laundering money or integrating illegal funds.
-
Provides a clear audit trail for regulatory authorities: Maintaining thorough documentation allows organizations to show compliance and offers a clear audit trail for investigations.
-
Helps identify potential financial crimes early: Detailed analysis of financial records can uncover suspicious patterns, allowing early intervention.
-
Establishes the legitimacy of business relationships: Verifying the source of wealth builds trust and strengthens relationships by ensuring clients use legitimate funds.
Challenges and Considerations:
-
Highly invasive process requiring extensive documentation: Gathering and analyzing detailed documentation can be complex and time-consuming, straining resources.
-
Difficulty verifying complex international wealth sources: Tracing wealth from multiple jurisdictions or involving complex ownership structures can be challenging.
-
Time-consuming analysis requiring specialized expertise: Effective analysis requires skills and experience in financial investigation.
-
May deter legitimate high-net-worth customers: Some clients may find the extensive documentation intrusive and may take their business elsewhere.
Examples of Successful Implementation:
Stringent source of wealth requirements are seen in places like Switzerland, Singapore, and Luxembourg. There, private banks and financial institutions follow strong EDD practices for high-net-worth individuals. These institutions often use specialized wealth intelligence services and risk-based thresholds for documentation requirements.
Actionable Tips for Implementing Effective Source of Wealth and Funds Documentation:
-
Create standardized documentation checklists: Develop specific checklists for different wealth sources (e.g., business ownership, inheritance, investments) to ensure consistent data collection.
-
Use third-party wealth intelligence services: Leverage specialized databases and investigative services to verify information and spot potential risks.
-
Implement risk-based thresholds for documentation requirements: Adjust the level of scrutiny based on customer and transaction risk.
-
Train staff to identify red flags in wealth documentation: Equip compliance teams to recognize suspicious patterns and inconsistencies in financial records.
By implementing a solid Source of Wealth and Funds Documentation process in an enhanced due diligence checklist, organizations can strengthen defenses against financial crime and ensure the integrity of their business relationships.
3. How to Identify and Monitor Politically Exposed Persons (PEPs) Effectively
Politically Exposed Person (PEP) screening and monitoring is crucial for an enhanced due diligence checklist. This is especially important for financial institutions and organizations subject to anti-money laundering (AML) and know-your-customer (KYC) regulations. This process identifies and monitors individuals in prominent public positions, along with their family members and close associates. Because of their influence and access to public funds, these individuals pose a higher risk for corruption, bribery, and money laundering. Strong PEP screening and monitoring procedures are essential to manage these risks and meet international standards. This includes screening against comprehensive PEP databases, assessing political risk exposure, and applying enhanced monitoring to detect suspicious activities.
PEP screening typically uses specialized software and databases with profiles of known PEPs across various jurisdictions. This automated screening allows organizations to quickly spot potential PEPs among their customers or during onboarding. The process involves family members and close friends. It can be complex because you need to identify relationships accurately. Modern systems use techniques like name matching and network analysis to uncover these connections. The system evaluates the political risk linked to identified PEPs, considering their position, political stability in their country, and any known corruption allegations. This risk assessment guides the level of enhanced due diligence applied to the PEP relationship. Ongoing monitoring is vital. It tracks changes in a PEP’s status, such as leaving office or facing new allegations, ensuring the risk assessment stays current.
Several major financial institutions have implemented successful PEP screening and monitoring programs. For example, Standard Chartered checks PEP lists in more than 60 markets. They also monitor and assess risks regularly. BNP Paribas has created a better PEP monitoring system. It uses advanced analytics to find suspicious transactions. Santander built an automated system to detect PEPs and score risks. This tool helps make compliance easier. These examples show that PEP screening and monitoring are effective in large financial firms.
To help organizations boost their PEP screening and monitoring, here are some key tips:
-
Utilize multiple PEP databases: Relying on one database can leave gaps. Using several trusted databases gives a wider view. It also lowers the chance of missing key information.
-
Combine automated screening with expert review. Automated systems work well, but trained compliance pros must check for false positives. They also need to investigate complex cases.
4. What’s the best approach for screening customers against sanctions and watchlists?
Sanctions and watchlist screening is a critical component of any enhanced due diligence checklist. In today’s increasingly interconnected global landscape, organizations face significant risks associated with engaging in transactions with sanctioned individuals, entities, or those involved in illicit activities like terrorist financing and money laundering. Failure to implement robust screening measures can result in severe regulatory penalties, reputational damage, and even criminal prosecution. This step goes beyond basic KYC (Know Your Customer) checks and delves deeper into the background of potential business partners, customers, and investors, making it an indispensable part of an enhanced due diligence checklist.
This process involves cross-referencing individuals and entities against a multitude of global sanctions lists, law enforcement watchlists, and politically exposed persons (PEPs) databases. These lists are maintained by various government agencies and international organizations, such as the Office of Foreign Assets Control (OFAC) in the US, the United Nations, and the European Union. The screening process aims to identify potential matches between the parties involved in a transaction and individuals or entities listed on these databases.
How does it work? Sanctions and watchlist screening utilizes sophisticated software solutions capable of handling vast amounts of data. These systems leverage features like:
- Real-time screening against multiple sanctions databases: This allows immediate flagging of potential matches at the point of transaction initiation, preventing engagement with prohibited parties.
- Fuzzy matching algorithms for name variations: These algorithms account for spelling errors, aliases, and different transliterations, increasing the accuracy of the screening process. This addresses the challenge of identifying individuals who may use slightly different names across different databases.
- Entity resolution for complex corporate structures: This feature unravels complex ownership structures and identifies ultimate beneficial owners (UBOs), ensuring that hidden connections to sanctioned entities are uncovered.
- Automated alert generation and case management: When a potential match is identified, the system automatically generates an alert and creates a case for further investigation. This streamlines the workflow and ensures that potential risks are addressed promptly.
- Historical transaction screening capabilities: This allows for retrospective screening of past transactions to identify potential past violations and mitigate future risks.
Implementing a comprehensive sanctions and watchlist screening program offers numerous benefits:
Pros:
- Prevents severe regulatory penalties and sanctions violations: By proactively identifying and mitigating risks, organizations can avoid hefty fines and legal repercussions.
- Protects against terrorist financing and criminal activity: Screening helps prevent unwitting involvement in illicit activities, safeguarding the organization’s reputation and contributing to global security.
- Maintains access to international banking networks: Demonstrating robust compliance with sanctions regulations is crucial for maintaining access to vital financial services.
- Provides comprehensive compliance audit trail: Thorough documentation of screening decisions provides evidence of due diligence efforts in case of regulatory scrutiny.
Cons:
- High volume of false positives requiring investigation: Common names and similar spellings can trigger false positives, necessitating manual review and investigation, which can be resource-intensive.
- Complex disambiguation of common names: Differentiating between individuals with similar names can be challenging and requires sophisticated algorithms and manual review processes.
- Constant updates required as lists change frequently: Sanctions lists are constantly updated, requiring organizations to maintain up-to-date databases and adapt their screening processes accordingly.
- Risk of business interruption during screening processes: Delays in screening can impact transaction processing times, potentially disrupting business operations.
Several organizations have successfully implemented robust sanctions screening programs after facing regulatory scrutiny. Wells Fargo, ING, and Standard Chartered have all invested heavily in enhancing their sanctions compliance programs following regulatory settlements, demonstrating the importance of these measures. These examples showcase how reacting to past failures can lead to robust systems that serve as a model for others.
Tips for Implementing Effective Sanctions Screening:
- Implement real-time screening at transaction initiation: This prevents engagement with sanctioned parties from the outset.
- Use advanced fuzzy matching with manual review processes: Combining automated technology with human oversight enhances accuracy and reduces false positives.
- Establish clear escalation procedures for potential matches: Define clear protocols for investigating and escalating potential matches to ensure timely and appropriate action.
- Maintain detailed documentation of screening decisions: A comprehensive audit trail provides evidence of due diligence and facilitates regulatory compliance.
Including sanctions and watchlist screening in your enhanced due diligence checklist is not just a best practice – it’s a necessity. By proactively addressing potential risks associated with sanctioned entities and individuals, organizations can protect themselves from financial and reputational damage, ensure compliance with international regulations, and contribute to a more secure global financial system. This step is crucial for any organization operating internationally or dealing with international clients, especially for roles like Chief Compliance Officer, Head of Compliance, Compliance Director, CFO, and Investor Relations Manager who bear the responsibility of regulatory adherence and financial integrity.
5. Enhanced Transaction Monitoring and Pattern Analysis
Enhanced transaction monitoring and pattern analysis represents a critical component of a robust enhanced due diligence (EDD) checklist. This sophisticated approach leverages advanced technologies, including machine learning and behavioral analytics, to move beyond basic “rules-based” transaction monitoring. It provides a dynamic and proactive method for identifying suspicious activity, ultimately mitigating financial crime risks and strengthening regulatory compliance. Instead of relying solely on predefined thresholds, this method learns from historical data and adapts to evolving criminal methodologies. This provides organizations with a more precise and comprehensive view of customer behavior, enabling the early detection of potentially illicit activities.
This technology works by analyzing vast datasets of transaction data to establish baseline customer behavior. Machine learning algorithms then identify deviations from this established norm, flagging potentially suspicious activities. These algorithms can detect subtle shifts in transaction patterns that might indicate money laundering, terrorist financing, or other financial crimes. For instance, a sudden increase in international wire transfers or a series of transactions just below reporting thresholds could trigger an alert. Behavioral analytics further refines this process by incorporating contextual information, such as customer demographics, geographic location, and transaction history, to provide a more holistic risk assessment. Real-time transaction scoring and risk assessment capabilities allow compliance teams to prioritize investigations and allocate resources effectively. Furthermore, cross-border transaction analysis provides crucial visibility into complex international fund flows, a common vector for illicit finance.
Several prominent financial institutions have successfully implemented enhanced transaction monitoring systems. HSBC, for example, invested $2.4 billion in financial crime compliance systems, incorporating advanced analytics to strengthen its AML program. Bank of America also employs a sophisticated analytics platform for AML, leveraging machine learning to enhance detection capabilities. Danske Bank, following a significant money laundering scandal, significantly bolstered its monitoring systems, underscoring the importance of this technology in preventing future breaches. These examples demonstrate the growing adoption and effectiveness of enhanced transaction monitoring within the financial sector.
Implementing enhanced transaction monitoring offers several significant advantages. Early detection of suspicious activity patterns allows for timely intervention, preventing financial losses and reputational damage. The use of advanced analytics significantly reduces false positives, freeing up compliance resources and allowing investigators to focus on genuine threats. This proactive risk management capability strengthens an organization’s overall compliance posture and improves regulatory reporting accuracy.
However, there are also challenges associated with implementing this technology. High implementation and maintenance costs, including software licensing, hardware upgrades, and ongoing technical support, can be a significant barrier for some organizations. The system also requires specialized technical expertise to configure, manage, and interpret the results. Complex model validation and governance requirements necessitate rigorous oversight to ensure accuracy and fairness. Furthermore, the potential for algorithmic bias and discrimination must be carefully addressed through ongoing monitoring and model adjustments.
To effectively utilize enhanced transaction monitoring, organizations should consider the following tips:
- Establish baseline behavior patterns for effective anomaly detection: Accurate baselining is crucial for identifying deviations that may indicate suspicious activity.
- Combine multiple data sources for comprehensive analysis: Integrating data from various sources, including internal transaction records, customer databases, and external fraud databases, enriches the analysis and provides a more complete picture of customer behavior.
- Regularly validate and update monitoring algorithms: Criminal methodologies constantly evolve, necessitating regular review and updates to ensure the system remains effective.
- Train investigators to effectively use advanced analytics tools: Equipping compliance teams with the necessary skills to interpret and utilize the outputs of these systems is essential for maximizing their impact.
Incorporating enhanced transaction monitoring into your enhanced due diligence checklist is not merely a technological upgrade but a strategic imperative in today’s complex financial landscape. For Chief Compliance Officers, CFOs, and Investor Relations Managers, this technology provides a crucial tool for proactively managing risk, ensuring regulatory compliance, and protecting the organization’s reputation. This advanced approach is particularly relevant when dealing with high-risk customers, complex transactions, or geographically diverse operations, justifying its prominent place in the enhanced due diligence process.
6. Business Purpose and Relationship Justification
In the realm of enhanced due diligence, understanding the “why” behind a customer relationship is as crucial as understanding the “who.” Business Purpose and Relationship Justification, a critical component of any enhanced due diligence checklist, ensures that financial institutions aren’t just onboarding clients, but are strategically partnering with entities whose business aligns with their own. This process involves a thorough assessment and documentation of the legitimate reasons for establishing and maintaining each customer relationship, particularly those deemed high-risk. This item deserves its place on the checklist because it acts as a gatekeeper, filtering out potentially problematic relationships and bolstering the institution’s defense against regulatory scrutiny.
This method operates on the principle of justifiable risk. It requires institutions to delve deep into the client’s business model, expected transaction volumes and patterns, and the overall commercial rationale for the relationship. By evaluating the potential risks and rewards associated with each client, institutions can make informed decisions about whether the relationship is commercially viable and ethically sound. This ensures that high-risk relationships offer a suitable risk-return balance and aren’t solely driven by profit motives. The process involves several key features: detailed business case documentation requirements, analysis of expected transaction volume and patterns, a comprehensive commercial rationale assessment, the application of risk-return evaluation frameworks, and ongoing relationship value monitoring.
Successful implementation of this process can be observed in various financial sectors. Private banks, for instance, often require extensive business purpose documentation from ultra-high-net-worth individuals (UHNW) before onboarding them as clients. Commercial banks utilize specific justification frameworks for clients operating in high-risk jurisdictions, ensuring compliance with international regulations and minimizing exposure to financial crime. Investment banks, when dealing with complex structured products, conduct enhanced due diligence focusing on the underlying economic purpose and legitimacy of these instruments.
To effectively implement Business Purpose and Relationship Justification, consider these actionable tips:
- Establish clear criteria for relationship approval at different risk levels: This provides a standardized framework for evaluating client relationships based on their inherent risk.
- Document expected vs. actual transaction patterns regularly: This allows for early detection of anomalies and potential red flags.
- Involve senior management in high-risk relationship decisions: This adds another layer of oversight and ensures strategic alignment.
- Create standardized business justification templates: This streamlines the documentation process and promotes consistency.
While this process offers significant advantages, including ensuring the commercial viability of high-risk relationships, providing clear documentation for regulatory inquiries, and supporting strategic business decision-making, it also presents certain challenges. The assessment can be subjective, requiring experienced judgment, and accurately quantifying relationship value can be difficult. It may also limit business development opportunities if applied too stringently. Finally, the process necessitates ongoing reassessment as relationships evolve.
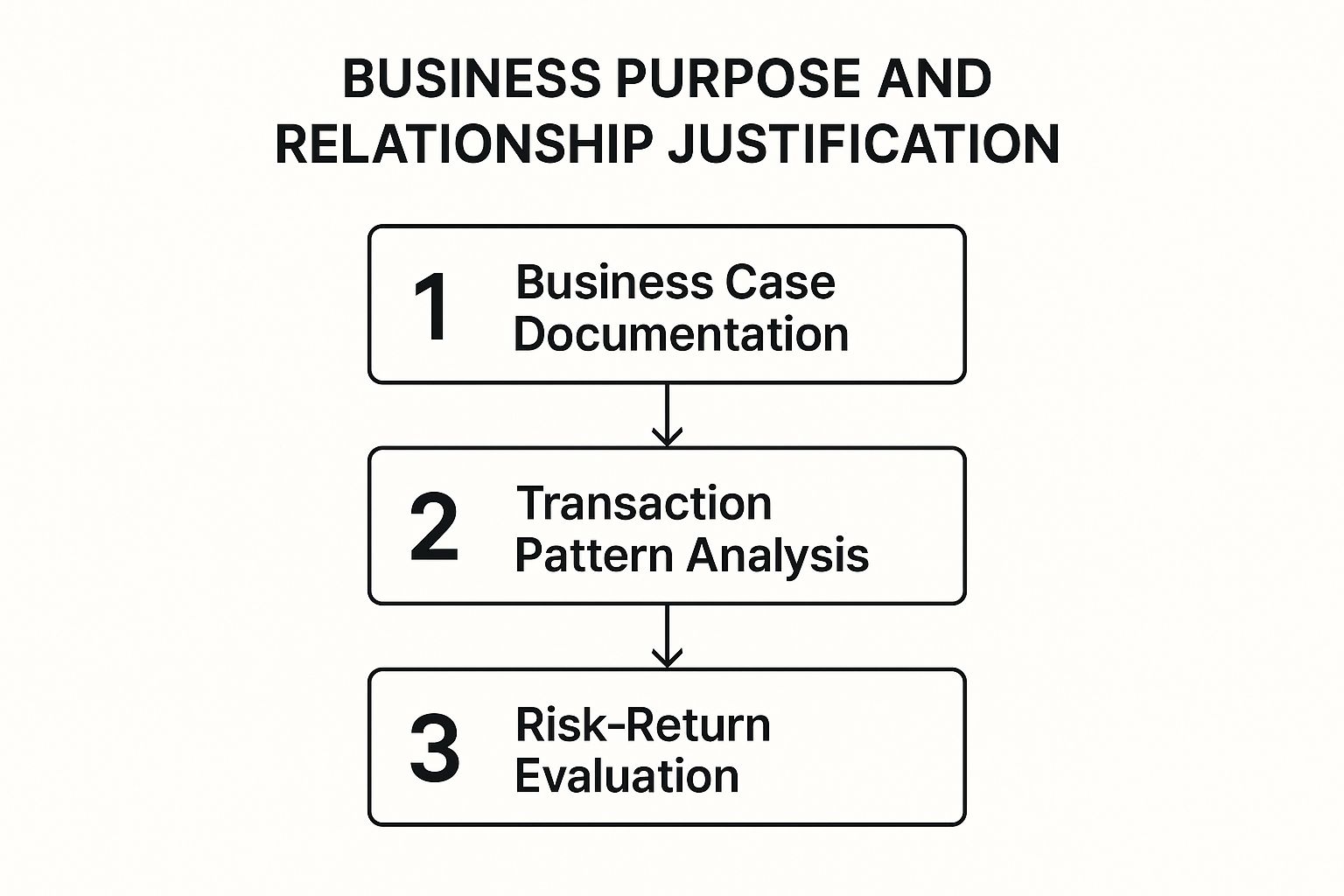
The following infographic illustrates the key steps involved in the Business Purpose and Relationship Justification process. It outlines the sequential flow from documenting the business case to analyzing transaction patterns and finally evaluating the risk-return profile.
The infographic visualizes a streamlined three-step process for justifying high-risk business relationships. Beginning with comprehensive Business Case Documentation, the process progresses to analyzing Transaction Pattern Analysis before concluding with a thorough Risk-Return Evaluation. The sequential nature of the process underscores the importance of establishing a solid foundation of understanding before assessing risk and potential return. This systematic approach ultimately empowers institutions to make well-informed decisions about client relationships, fostering both growth and security.
By diligently applying the principles of Business Purpose and Relationship Justification, financial institutions can navigate the complexities of the modern financial landscape with confidence, ensuring sustainable growth while mitigating potential risks. This process, while demanding, is an indispensable element of any robust enhanced due diligence checklist, protecting institutions and contributing to the overall stability of the financial system.
7. How do you maintain continuous compliance through monitoring and periodic reviews?
A robust enhanced due diligence (EDD) checklist must include ongoing monitoring and periodic review requirements. This critical component ensures that the initial risk assessment remains relevant and reflects the dynamic nature of customer relationships. Without continuous monitoring, a business risks exposure to evolving threats, regulatory penalties, and reputational damage. This section explores the importance of ongoing monitoring and periodic reviews within an enhanced due diligence framework, offering actionable tips for successful implementation.
Ongoing monitoring and periodic review establish a systematic framework for continuous scrutiny of high-risk customers. This process involves regular reviews, updated risk assessments, and enhanced surveillance activities. It’s a proactive approach that moves beyond the initial onboarding checks, ensuring that the understanding of customer risk profiles remains current. This is particularly critical in today’s rapidly changing regulatory and financial landscape.
How it Works:
The process begins with establishing a risk-based approach to review frequency. Higher-risk customers require more frequent reviews, while lower-risk customers can be reviewed less often. This risk-based approach optimizes resource allocation without compromising compliance. Automated monitoring triggers and alerts, based on pre-defined criteria, streamline the process. For example, significant changes in transaction volume, geographic location, or business ownership can trigger an immediate review.
Comprehensive risk reassessment procedures form the core of this ongoing monitoring. These procedures should encompass an updated Know Your Customer (KYC) review, revisiting the source of funds and wealth, and reassessing the customer’s overall risk profile. Customer information update requirements ensure that the business maintains accurate and current data on its customers. This might include periodic requests for updated identification documents, proof of address, or business registration information. Finally, enhanced surveillance activity monitoring provides an additional layer of scrutiny, tracking customer transactions and activities for any suspicious patterns or red flags.
Features of Effective Ongoing Monitoring and Periodic Review:
- Risk-based review frequency determination: Tailoring the review frequency to the inherent risk of the customer.
- Automated monitoring triggers and alerts: Systematically flagging changes in customer behavior or profile.
- Comprehensive risk reassessment procedures: A structured approach to reassessing customer risk.
- Customer information update requirements: Ensuring data accuracy and relevance.
- Enhanced surveillance activity monitoring: Continuously analyzing customer transactions and activities.
Benefits of Implementation:
- Maintains current understanding of customer risk profiles: Providing a dynamic view of risk, crucial in a changing environment.
- Enables proactive risk management and early intervention: Identifying potential issues before they escalate.
- Ensures ongoing regulatory compliance: Meeting regulatory expectations for ongoing due diligence.
- Facilitates timely relationship decisions and adjustments: Providing the information needed to adjust customer relationships as risk profiles change.
Challenges and Considerations:
- Resource-intensive ongoing monitoring requirements: Implementing and maintaining an effective program requires significant resources.
- Difficulty in determining appropriate review frequencies: Balancing thoroughness with efficiency in setting review schedules.
- Challenge of maintaining customer engagement during reviews: Ensuring a positive customer experience throughout the review process.
- Complex coordination across multiple business units: Effective implementation requires collaboration across different departments.
Examples of Successful Implementation:
Several leading financial institutions have successfully implemented robust ongoing monitoring programs. Citi’s enhanced periodic review program for correspondent banking provides a strong example of a risk-based approach to ongoing due diligence. UBS’s systematic monitoring framework for wealth management clients demonstrates the use of technology to automate and streamline the process. Barclays’ automated review triggering system for high-risk customers exemplifies the use of data analytics to proactively identify potential risks.
Actionable Tips for Implementation:
- Establish clear review calendars based on risk ratings: Create a structured schedule for reviews, ensuring that higher-risk customers are reviewed more frequently.
- Use automated systems to trigger reviews based on activity changes: Implement technology to monitor customer activity and automatically trigger reviews when pre-defined thresholds are met.
- Create standardized review templates and checklists: Develop consistent procedures for conducting reviews to ensure thoroughness and efficiency.
- Implement quality assurance processes for review completeness: Regularly assess the effectiveness of the ongoing monitoring program and identify areas for improvement.
Including ongoing monitoring and periodic review in your enhanced due diligence checklist is crucial for managing risk effectively. By proactively identifying and mitigating potential threats, organizations can protect themselves from financial losses, regulatory penalties, and reputational damage. This proactive approach is not merely a checkbox in the compliance process; it’s a cornerstone of a robust risk management framework. For senior management, including the Chief Compliance Officer, Head of Compliance, Compliance Director, CFO, and Investor Relations Manager, understanding and implementing this component of EDD is critical for maintaining a strong risk and compliance posture.
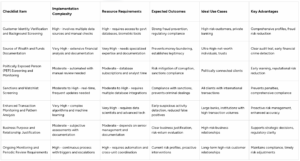
Enhanced Due Diligence Checklist Comparison
Staying Ahead with a Robust Enhanced Due Diligence Program
In today’s complex regulatory landscape, a robust enhanced due diligence checklist is no longer a luxury but a necessity. This article has outlined seven critical components of a comprehensive program, from customer identity verification and background screening to ongoing monitoring and periodic review requirements. Mastering these elements, including politically exposed person (PEP) screening and sanctions and watchlist screening, allows your institution to move beyond a basic KYC checklist and delve deeper into potential risks. A thorough enhanced due diligence program enables you to proactively identify red flags related to source of wealth and funds, unusual transaction patterns, and the true purpose behind business relationships. Remember, a well-defined business purpose and relationship justification is key to understanding your client’s activities.
Implementing these enhanced due diligence best practices translates directly to a stronger risk management framework and ensures your organization remains compliant with evolving regulations. This not only protects your institution from financial penalties and reputational damage but also fosters trust and transparency with your clients and stakeholders. By prioritizing a proactive approach to compliance, particularly in areas like enhanced transaction monitoring and analysis, you demonstrate a commitment to ethical business practices and solidify your standing in the market.
Taking the next step towards implementing a truly effective enhanced due diligence program requires a commitment to continuous improvement and adaptation. Consider leveraging technology solutions that automate workflows and enhance your existing processes. By investing in a robust system, you can streamline your efforts, reduce manual workloads, and achieve greater efficiency in your compliance program. Embrace the power of a proactive and comprehensive enhanced due diligence checklist to safeguard your organization, build trust, and navigate the complexities of the modern financial world with confidence.